AWS Network
Steps
Create a custom VPC for you project. This is a entire private network therefore we specify a private IP range. Inside the VPC we create subnets with their own private ip. This VPC is placed with in a region and each subnet is placed within a availbility zone. Then we can deploy ec2 instances or other compute services on the subnet. Each resources can be assigned a private IP address and now all the resources within the VPC can communicate with each other even if they are at different availability zone.
Checkout the diagram below.
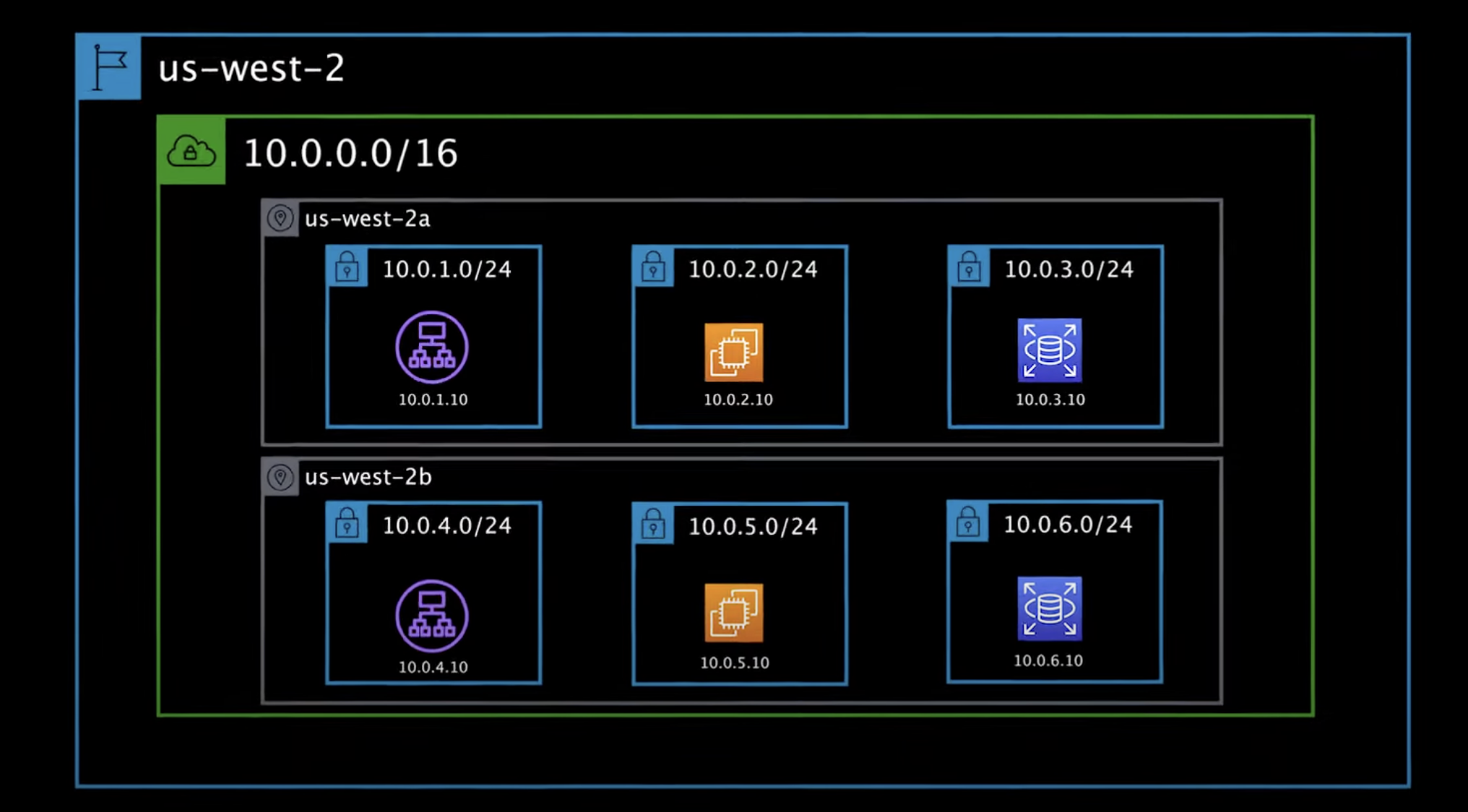
Now the VPC is completely private, the resource within the VPC can communicate within each other but they cannot access other VPC or access things in the internet.
Within a VPC we can add a internet gateway which allows open networking on the public internet. A Internet gateway can be attached to some of the subnet which will become a public subnet allowing it to access public internet. while the other subnet that do not have internet gateway will still remain private. for eg: web server is public while database is private.
Now if you want this private resources private however also want to communicate with other things outside of the VPC there are other services we can use. eg:
- S3 gateway to connect privately to s3 bucket.
- NAT Gateway to allow connection out of the private subnet with allowing public access to that subnet.
- etc.
The Default VPC
The default VPC provided by AWS is great for testing stuffs however they are not that great in production environment because they are completely open and they all have internet gateway which will make everything you deploy accessible to the internet.
Create your VPC
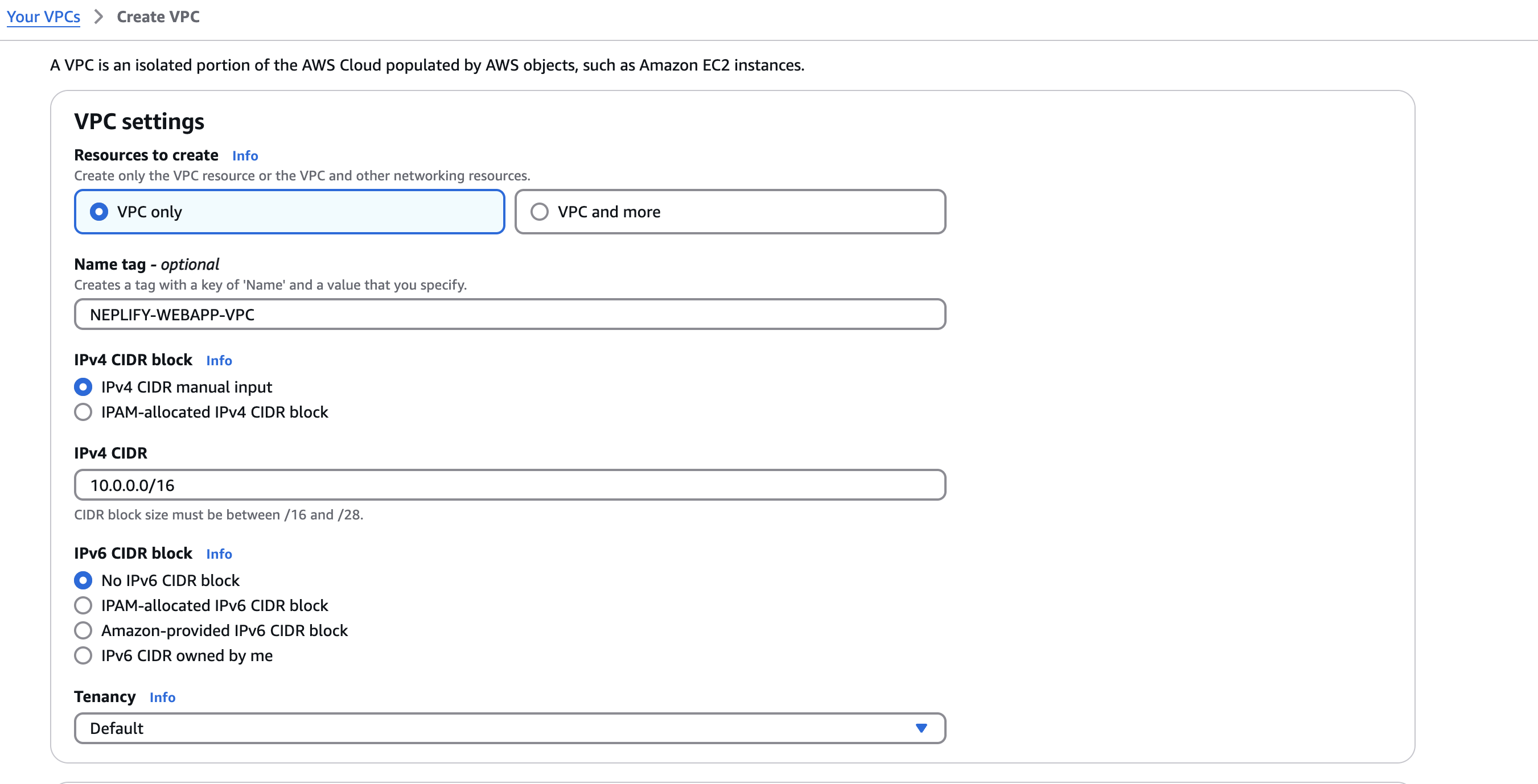
Here 16 in 10.0.0.0/16 represents the first 16 bit will be preserved i.e 10.0 and anything after that the other 16 bit (2^16=65,536) different ip addresses we can use withing this VPC and 16 is the minimum value supported by AWS.
CIDR - Classless Inter-Domain Routing
This is the private network address range that we can withing a VPC.
10.0.0.0
172.31.0.0
192.168.0.0Subnet
Creating a public subnet for the above VPC. Here in the CIDR Block 10.0.1.0/24.
10.0 has to be the first 2 digits because that is my VPC's CIDR and /24 means we are 24 of these bits are preserved that means 10.0.1 and only the last digit can be a variable for this subnet which will range till 256 (2 - 256) that would be total 255.
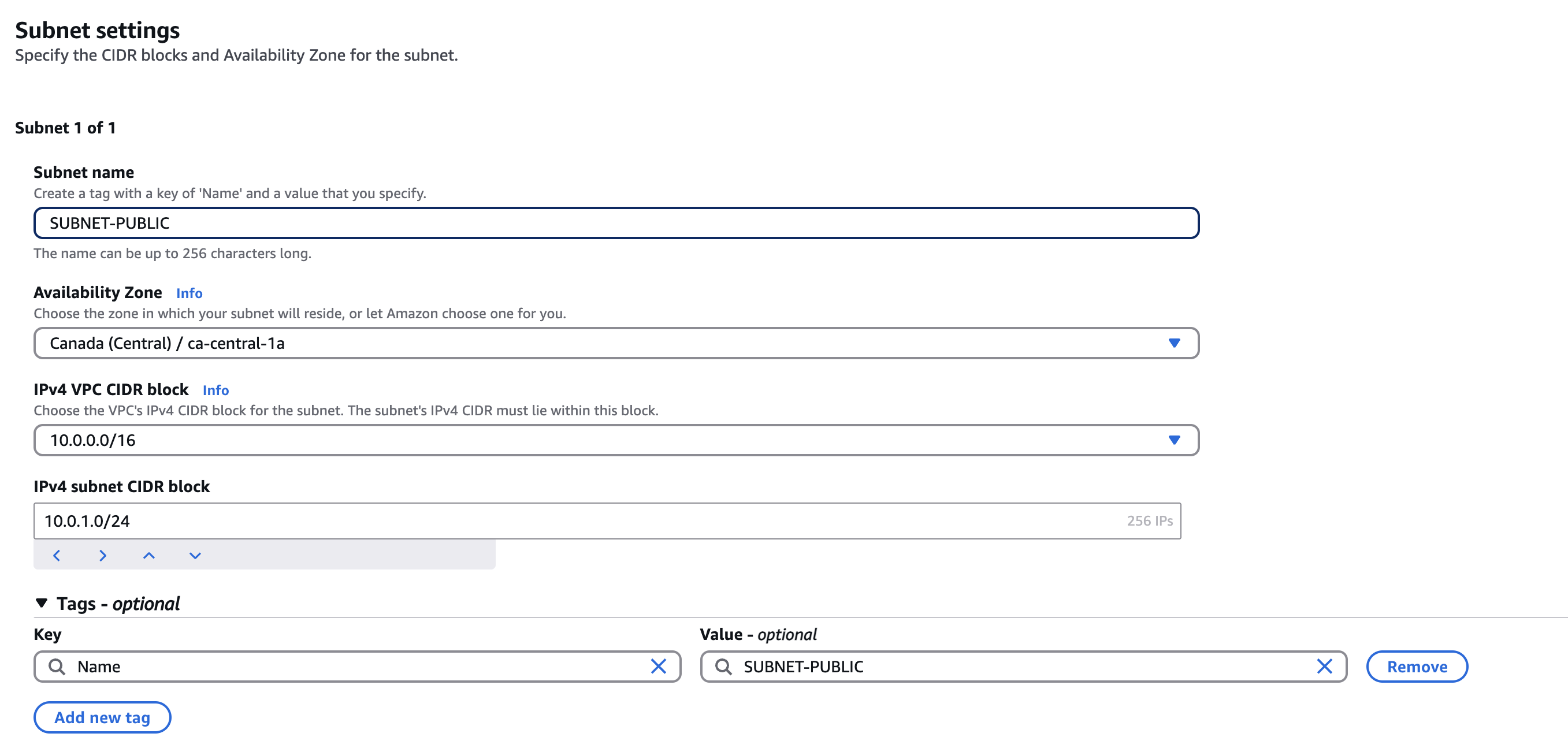
Also lets create a private subnet basically everything is some except the CIDR block, for private gateway we will allocate 10.0.2.0/24.
EC2
Now lets create a ec2 instance with this public VPC selected and in the process also create a security group with ssh and http inbound allowed.
If you try to ssh to this new ec2 you should notice you cannot to this instance it is because the VPC that was used to create ec2 does not have a internet gateway.
Internet Gateway.
To attach internet gateway to our VPC we need to do the following steps.
- Create Internet Gateway - Create a internet gateway
- Attach the gateway to the VPC - and once the internet gateway is created you should Action >
Attach to VPC - Create a route table. - A route table is a thing withing a VPC that manages where traffic goes. There should already be a default route table that is attached to your subnet which is responsible to handle traffic between your private networking.
Once you have the route table create click
Edit routesbutton Click Add with0.0.0.0/0(any ip) as your Destination and select the IGW that you created as your target now this will allow connections to and from for any subnet that is using this route table. - Attach a route table to public subnet. - Go to your public subnet on Route table tabs select
Edit route table associationand replace your default route table with the one with IGW.
Now you can ssh into your ec2 or also you can browse your public ip address (after you install nginx).
To Install NGINX on Amazon Linux 2023
cat /etc/os-release
sudo dnf install nginx -y
sudo systemctl enable nginx
sudo systemctl start nginx
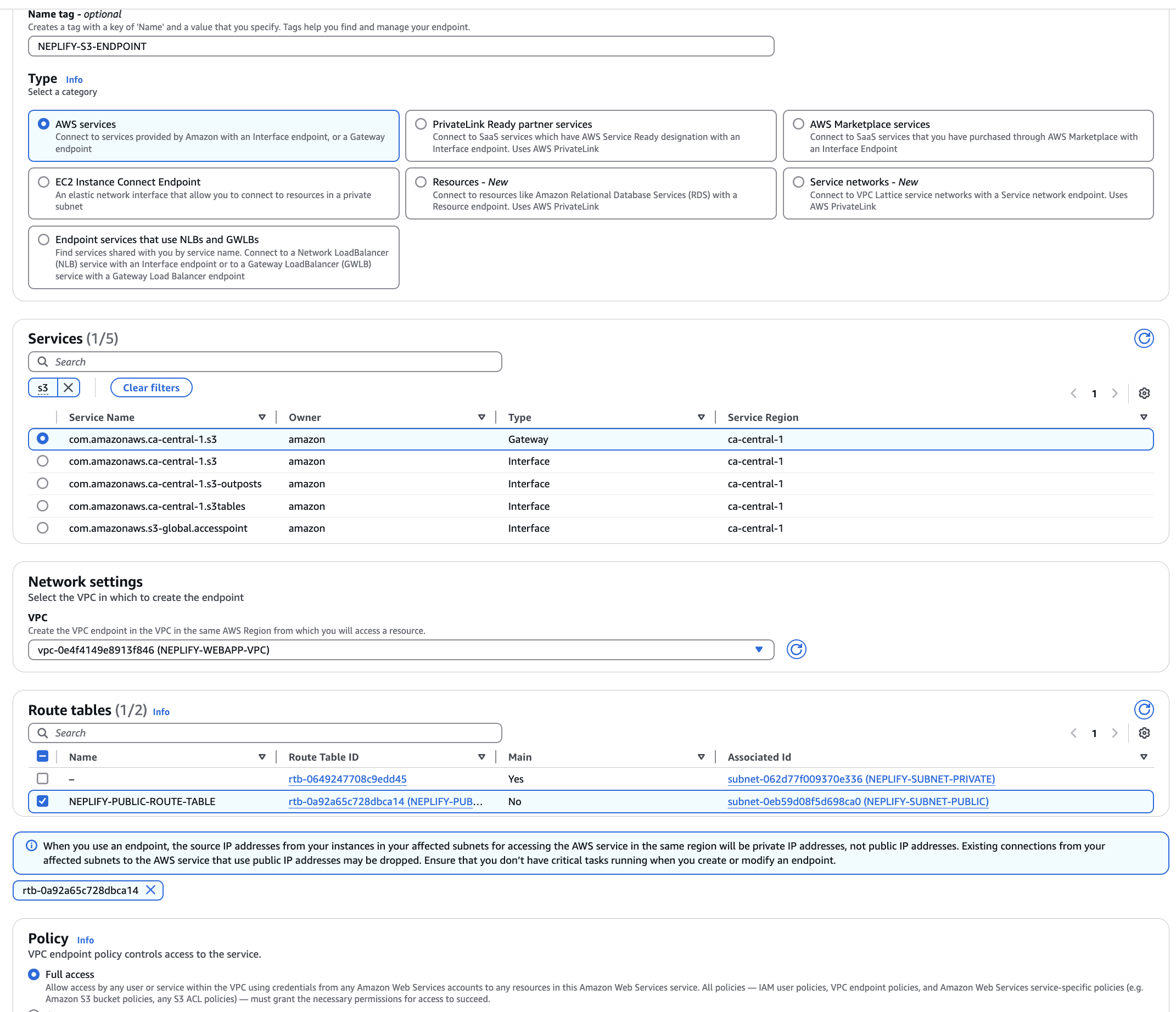
VPC Gateway Endpoint
With this you can connect from your private subnect to another aws services all through AWS private networking. There are many endpoints that you can create within a VPC one of that being endpoint to s3 bucket.
You can setup endpoints at VPC > Endpoints and Create Endpoints. Interface endpoint will cost money while gateway endpoint won't cost anything.
- Give it a name
- Type should be
AWS Service - Search s3 and Select com.amazonaws.ca-central-1.s3 (gateway)
- Select your VPC
- Select your route table to which you want attach this link
- Specify policy (default full access)